Windows Remote Management is no longer a way to think in today’s world. But why do we do it unencrypted? Normally the authentication is done by Kerberos. That’s secure enough for most people. However, Kerberos also has limitations, for example when using local accounts.
In the standard system, communication is via HTTP via TCP port 5985. Why not HTTPS? This is possible, the port TCP 5986 is intended for this. Unfortunately, this is not only missing in the firewall rule templates but also has a few barriers still in the way. We take care of these barriers today.
Prerequisites
These instructions are intended for a business environment correspondingly are the prerequisites.
- All computers are part of the same Active Directory domain
- An AD Integrated Certification Authority is available
- Automatic registration of corresponding certificates must be activated
Certificate template
For HTTPS we need an appropriate certificate for web services. For this, we adopt a corresponding template in the certification authority. To do this, duplicate the template “Webserver” in the certificate template console.
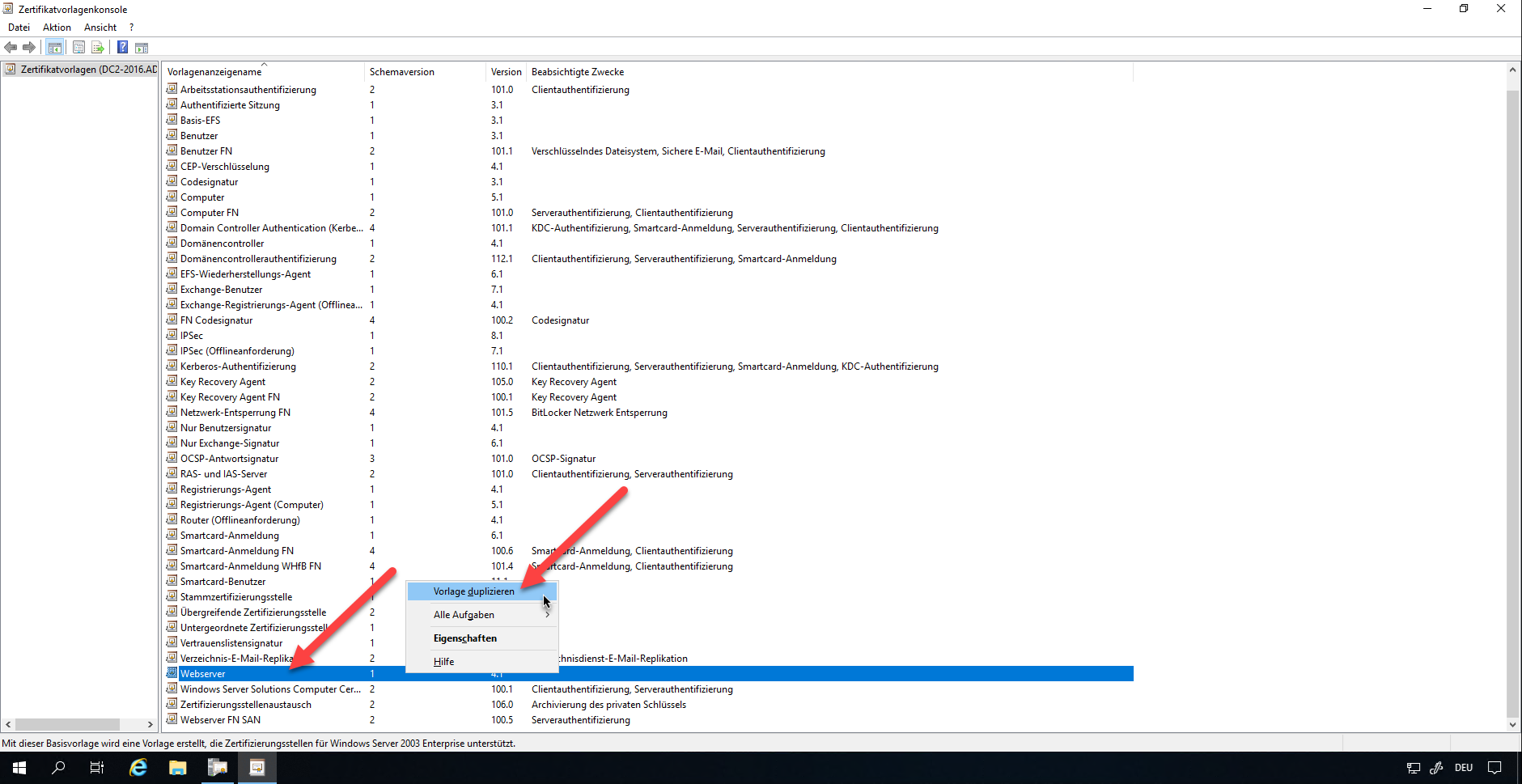
Adjust the compatibility settings according to your CA specifications. Enter an appropriate name in the “General” tab.
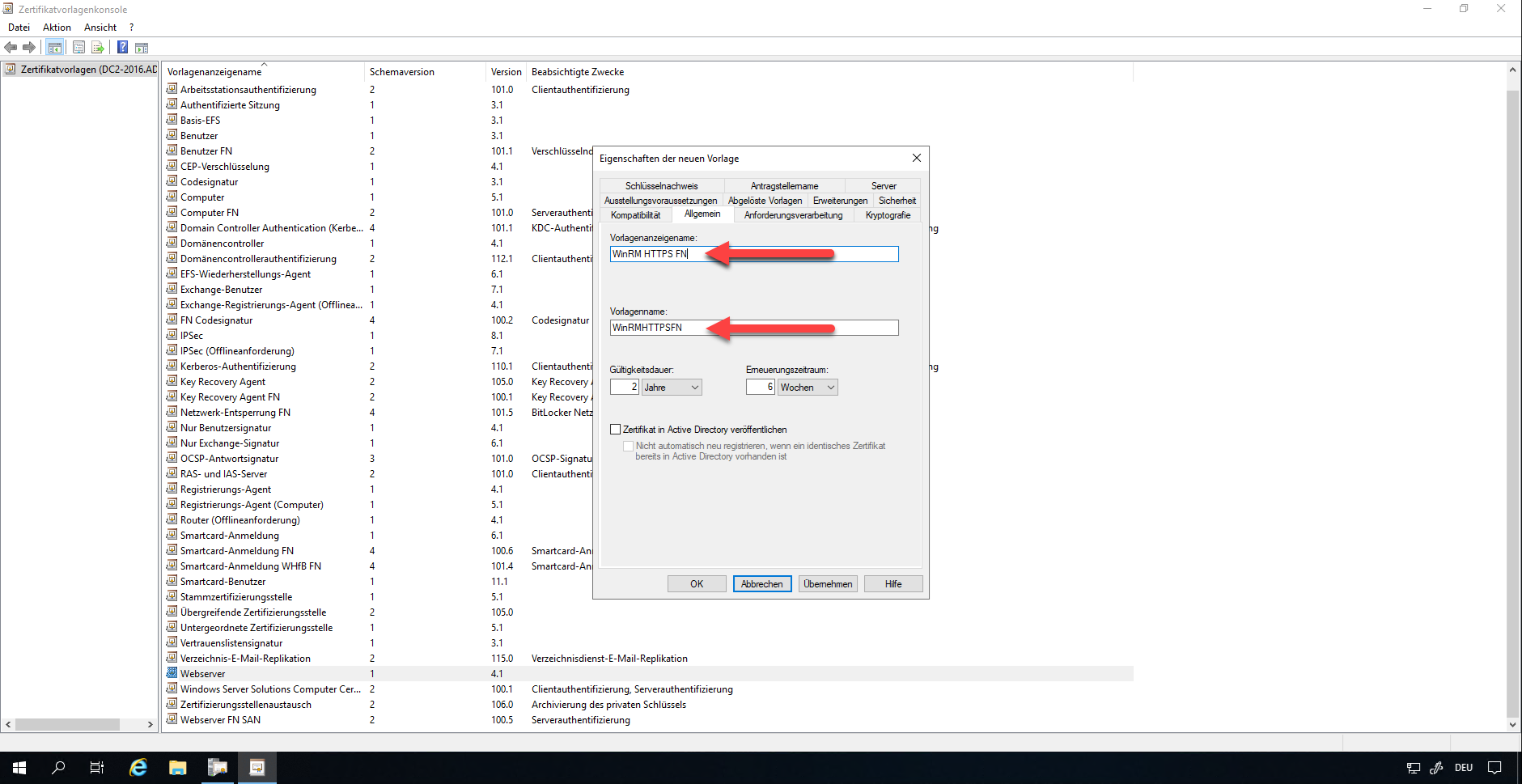
Under the tab “Applicant name” please select the options “Create from this information in Active Directory”. The format for the applicant name should be “General Name”. The information to include is only the DNS name.
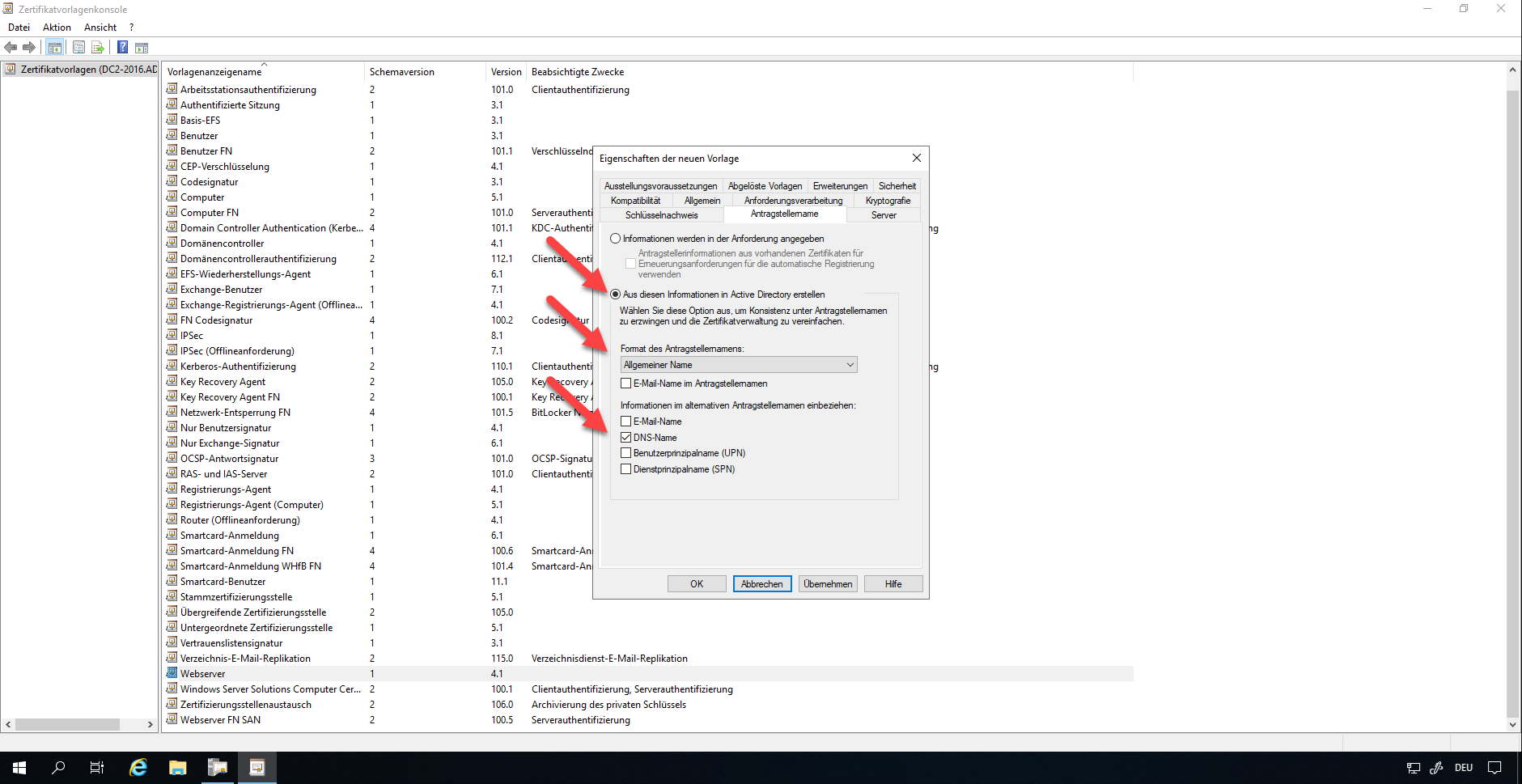
In the “Security” tab, the group of domain computers must be added. The required rights are Read, Register, Automatically register.
Save the template. Then switch back to the Certification Authority console. Under Certificate Templates, select New and Certificate Template to Issue.
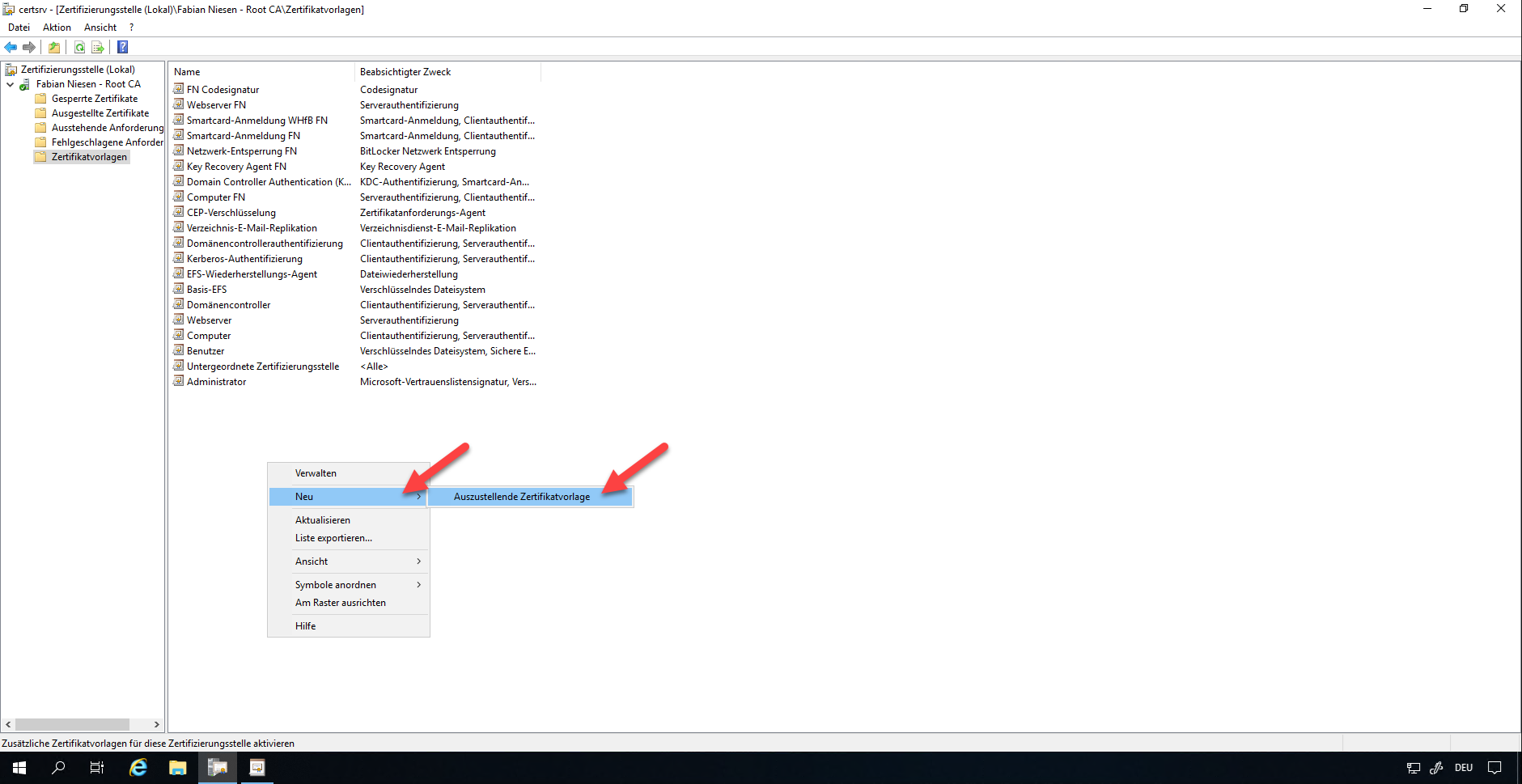
Now select the new template.
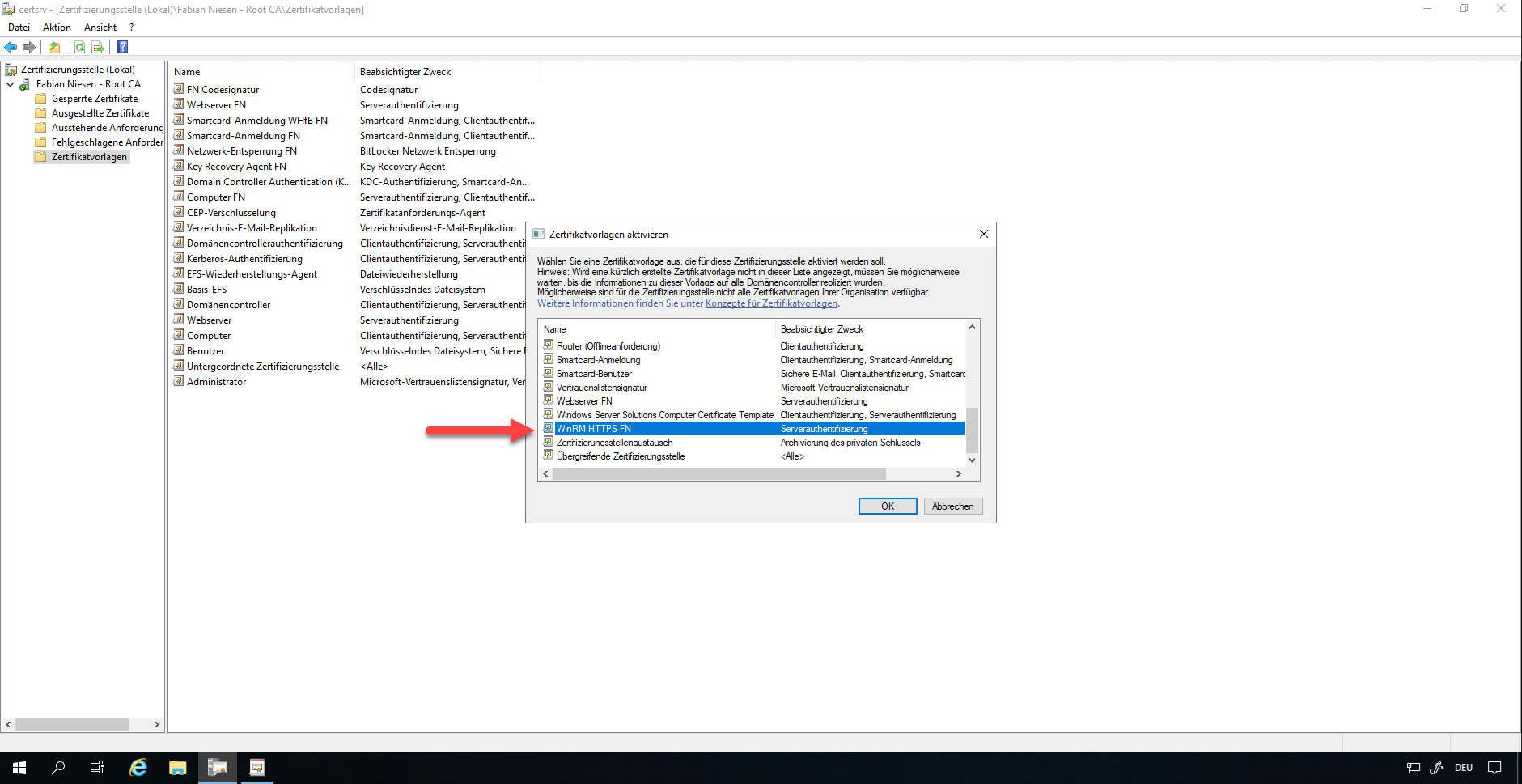
The next time the computers report to the certification authority, the corresponding certificates are issued.
Preparing the Group Policy
When the systems receive the certificates, we can take care of the group policy.
Firewall unlock
First, you should create the rules for the Windows firewall. Open the group policy and go to “Incoming rules” and create a new rule there.
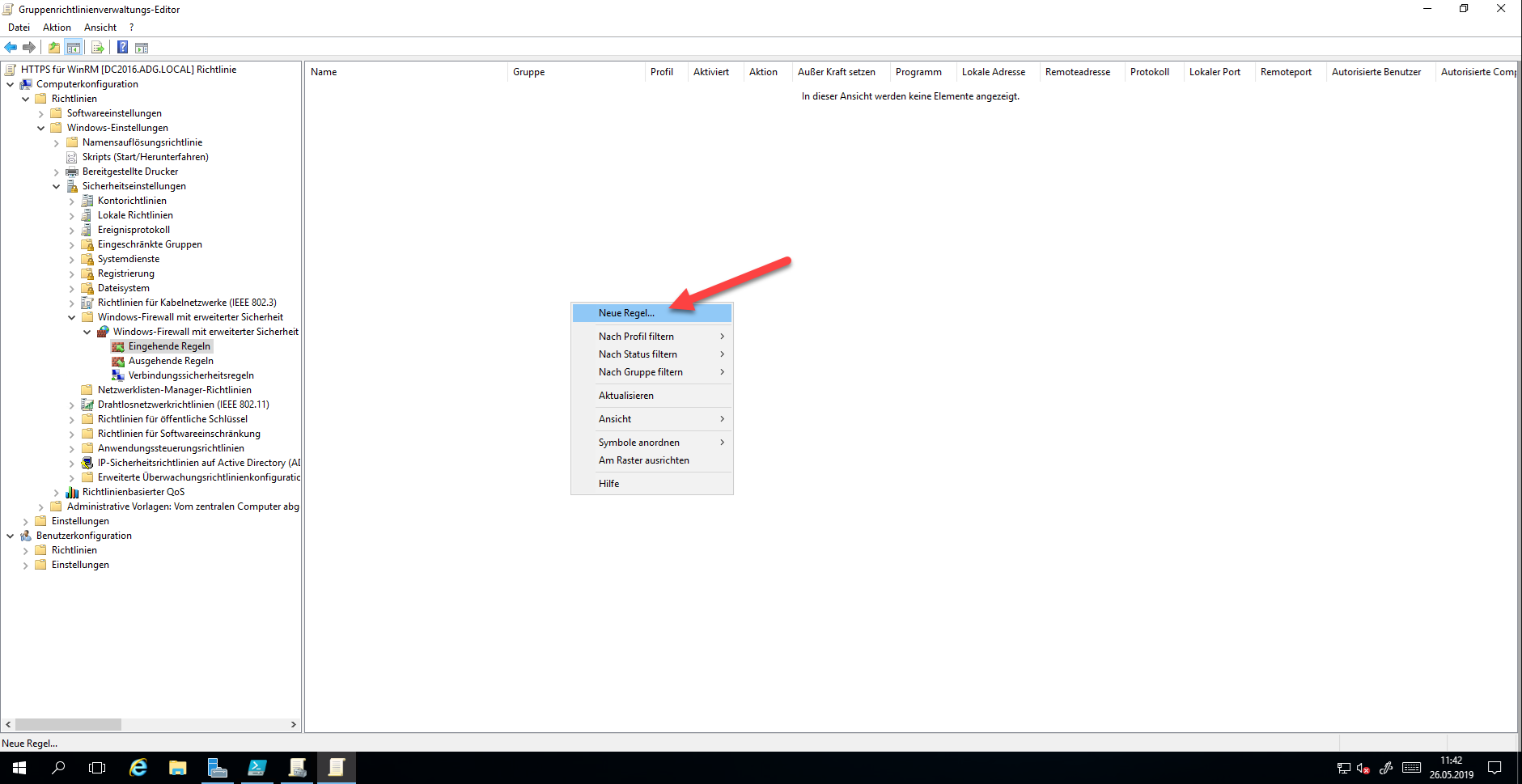
Create a Custom Rule
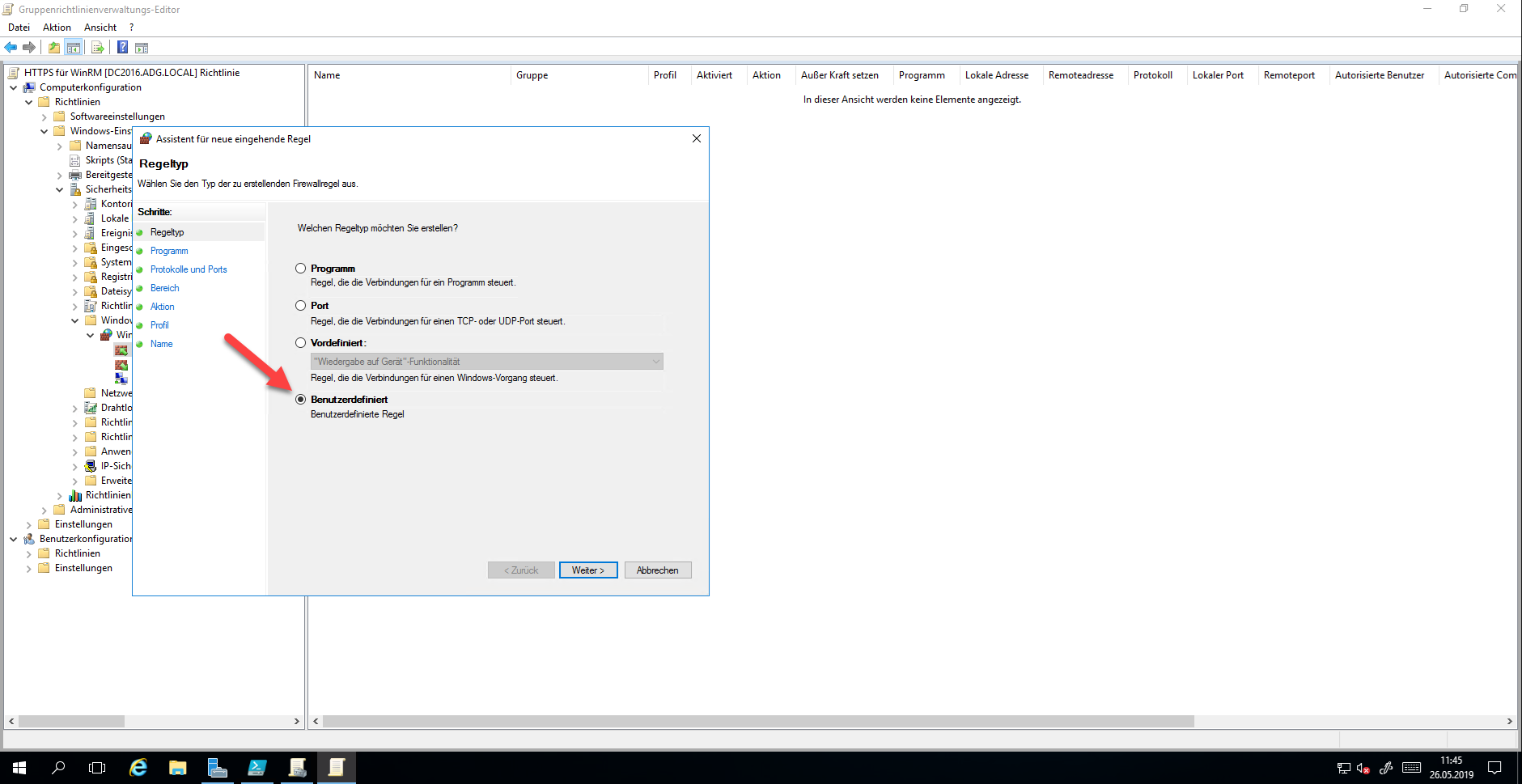
Enter “System” as the program path.
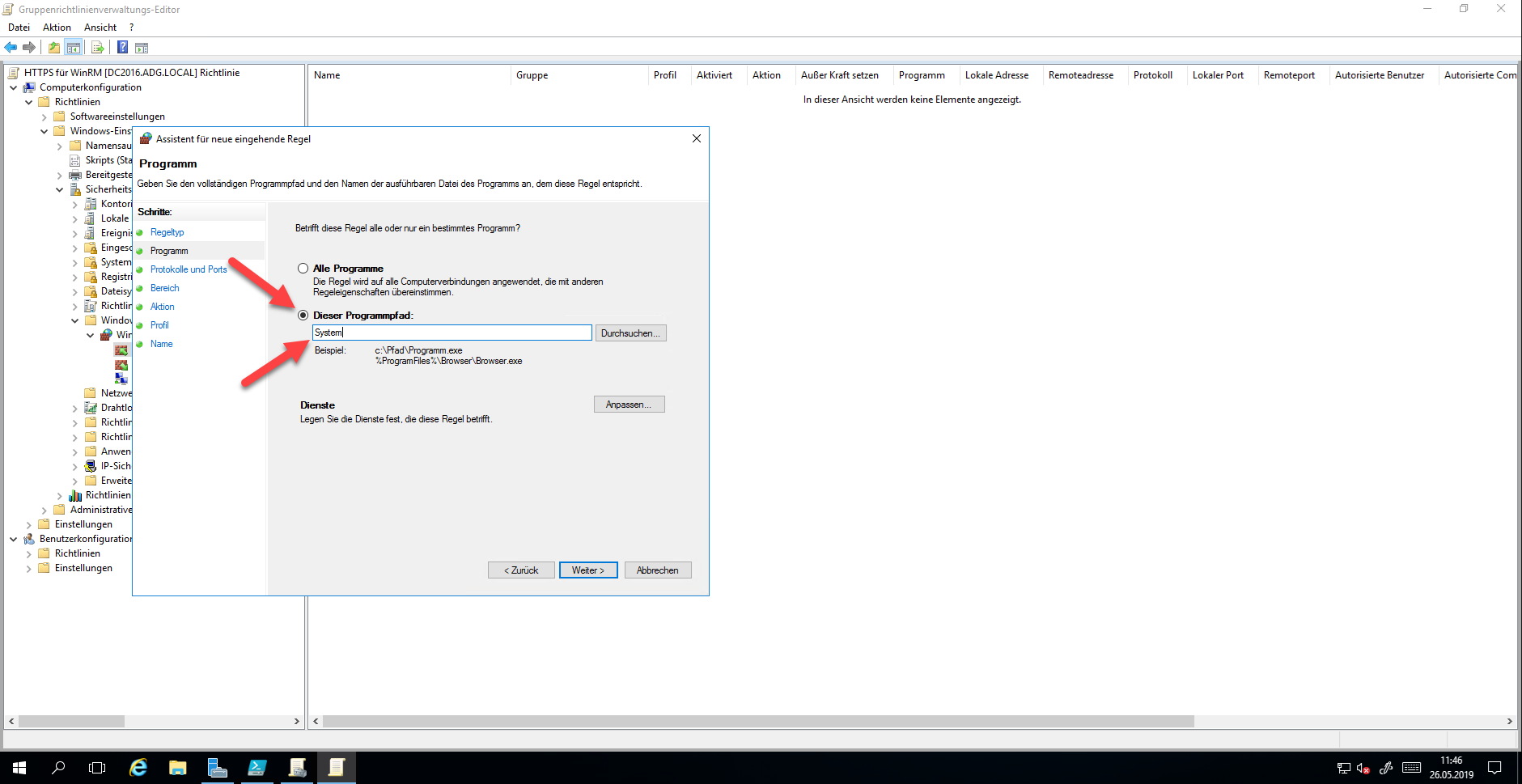
The following settings must be selected for configuring the protocols and ports:
- Protocol type: TCP
- Local Port: Specific Port
- Port Number: 5986
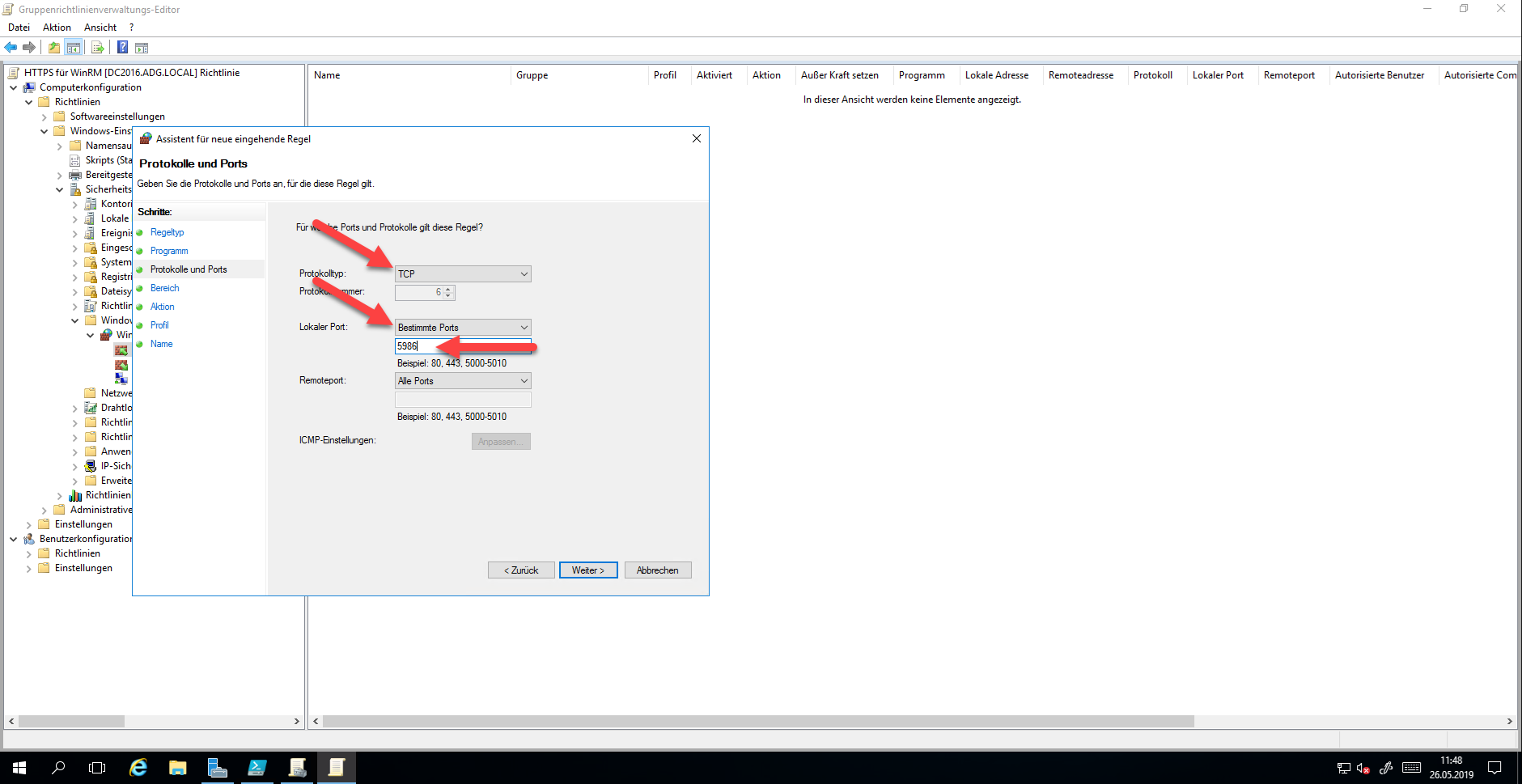
You can adjust the settings for Range as required. Select “Allow the connection” in the “Action” step. Only “Domain” should be selected as profile, otherwise, WinRM should not be allowed.
Choose a suitable name and create the firewall rule
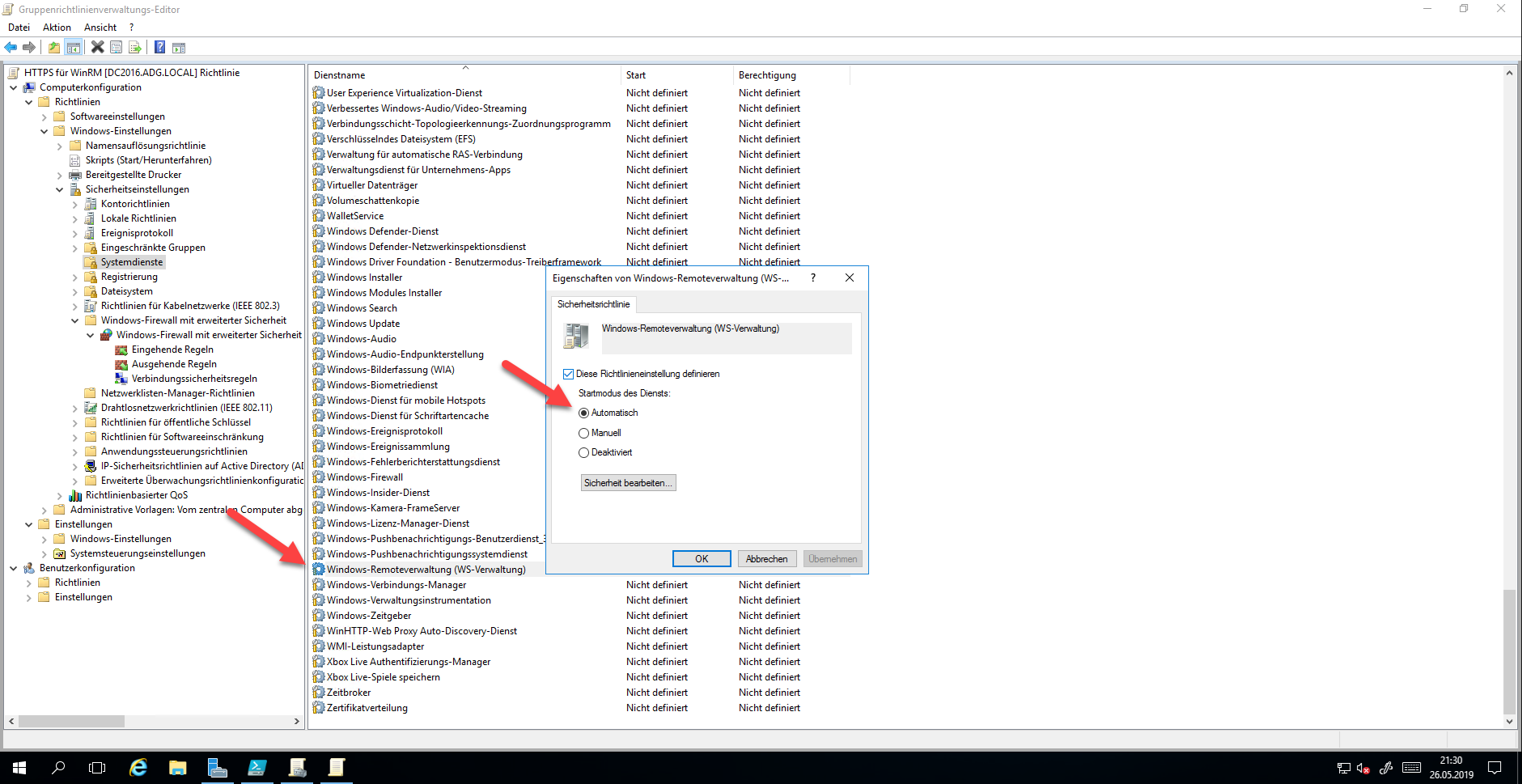
Configuring Services
With today’s operating systems, the Windows Remote Management Service should actually be started automatically. To be on the safe side, the service is set to start mode “Automatic” by the policy.
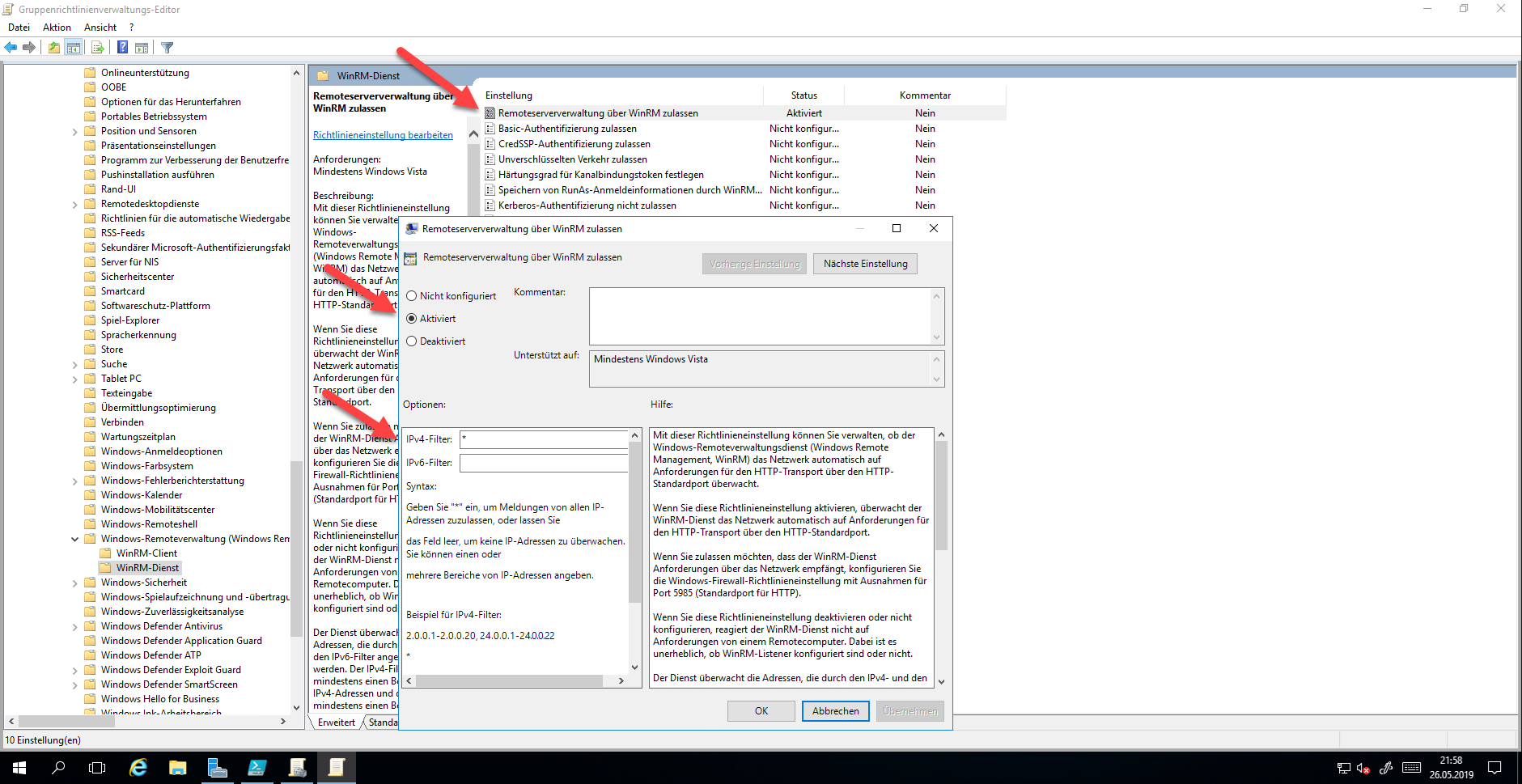
Configure WinRM Service Using Administrative Template
The next step is to configure the Windows RM Service with an administrative template. The settings can be found under Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRM Service > Allow Remote Management via WinRM.
In this setting, not only the service can be activated, but also the IP ranges from which the service can be reached. In further settings, you can find settings to control different authentication methods.
Configuring HTTPS for WinRM
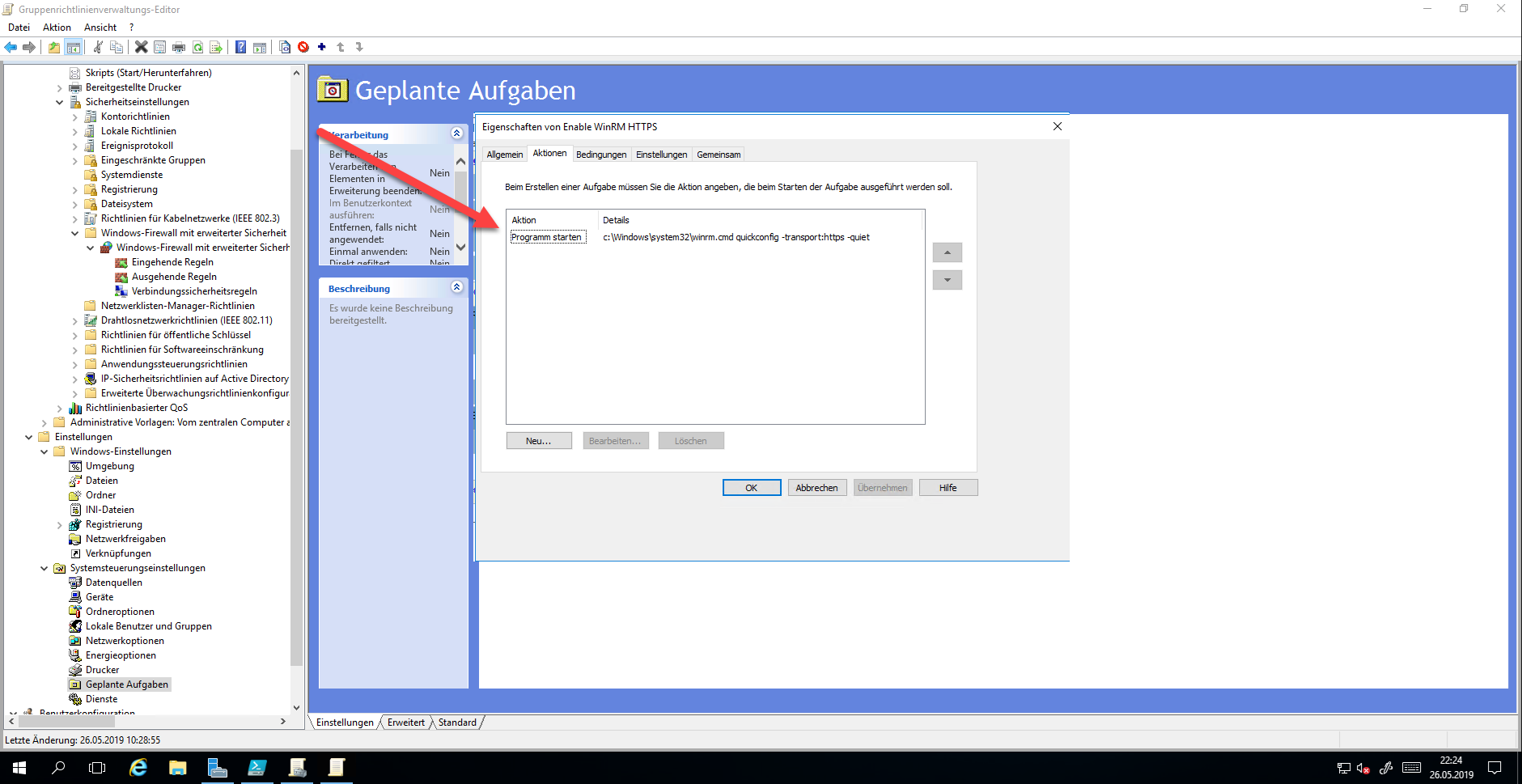
Unfortunately, WinRM cannot simply configure with a policy for HTTPS. This only works with the command “WinRM quickconfig -transport:https -quiet”. To make it easier, the command is configured as Instant Task.
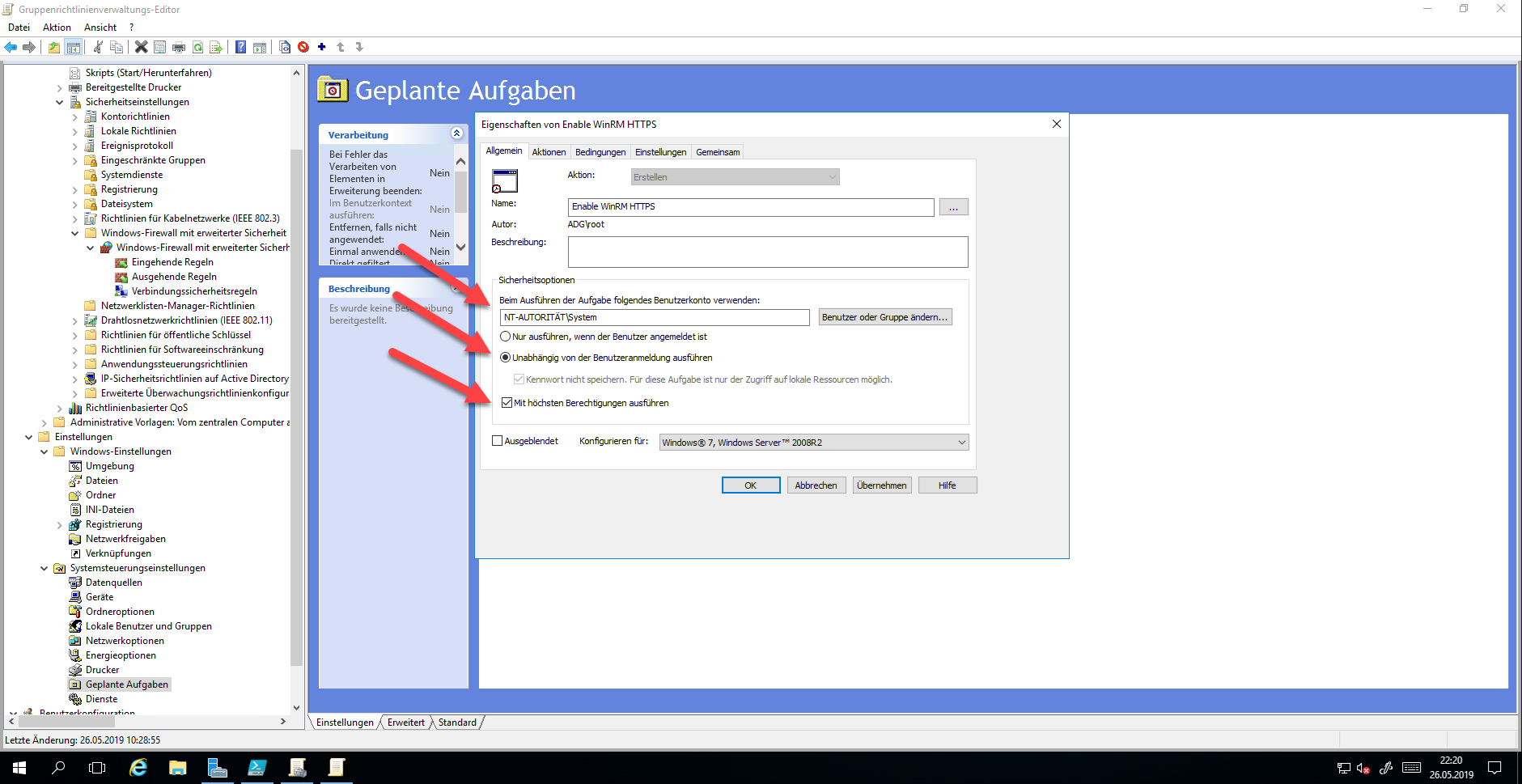
This executes the command immediately after Group Policy is applied.
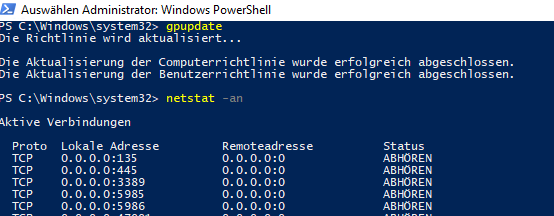
And already the port is open
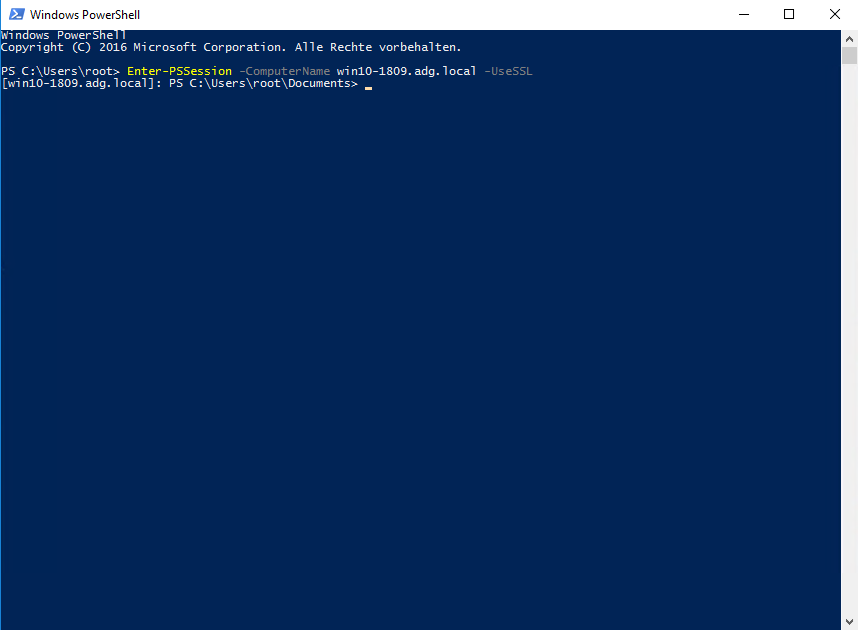
It is important to use the FQDN for the connection, otherwise, a certificate warning appears.
This article first appeared on Infrastrukturhelden.de in German.
This article is a translation of the Infrastrukturhelden.de article “Windows WinRM über HTTPs” (Published – 2019-05-28). Links may refer to other Infrastrukturhelden.de articles, these may also be available in English language.
Also it can be, that I still use screenshots of German systems. However, where it is possible for me with little effort, I insert screenshots of English systems.

