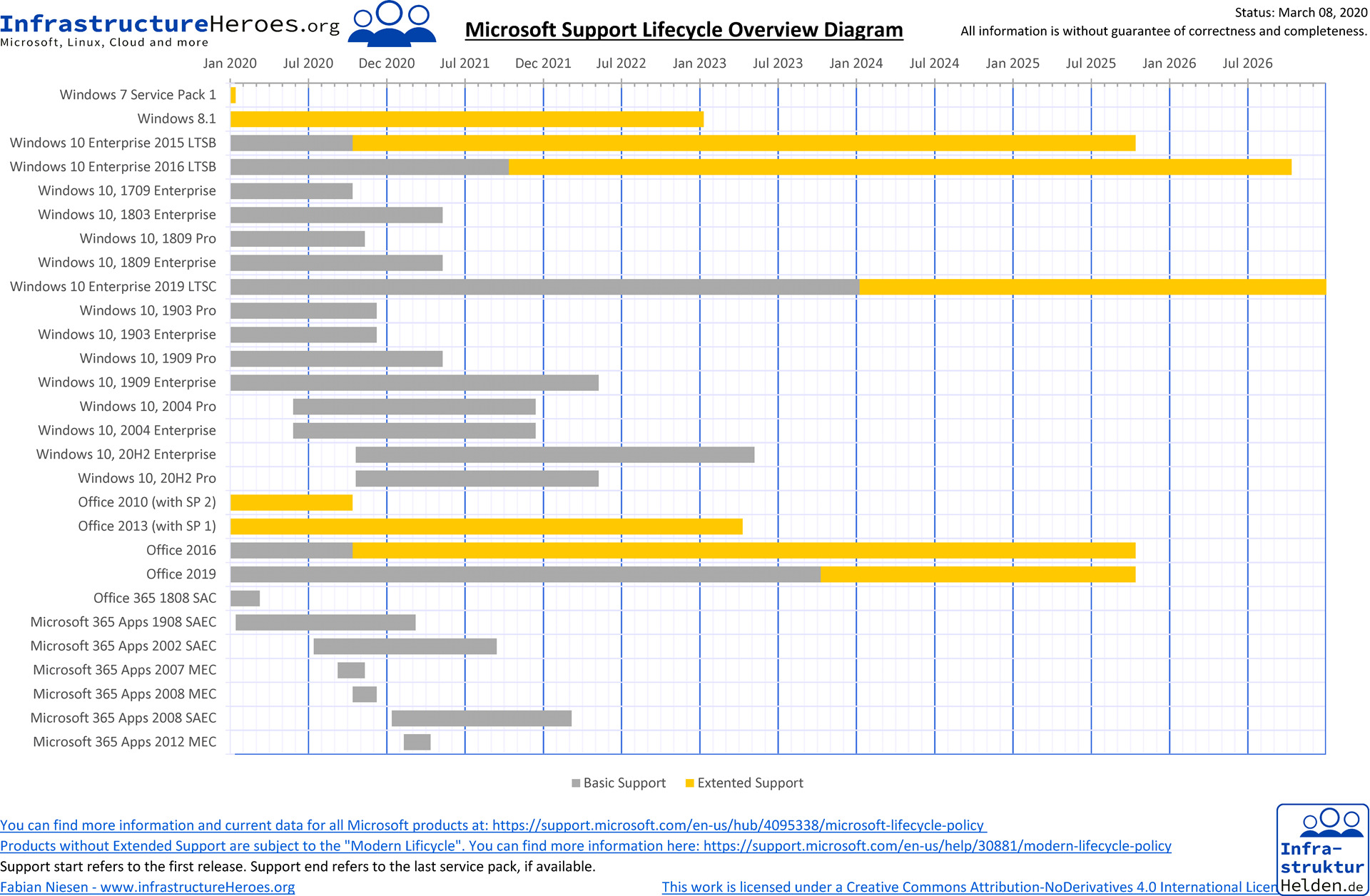
Especially in test environments, you often need an older release of Windows 10, but how can you set Windows to a target release? Many companies are currently still using Windows 10 1909, and the Enterprise Edition is still supported until 11.05.2022. Unfortunately, I can only defer the feature upgrade in Windows 10 for 365 days. This means that a newly installed Windows 10 1909 updates to 20H2.
Windows LAPS and the migration from Microsoft LAPS
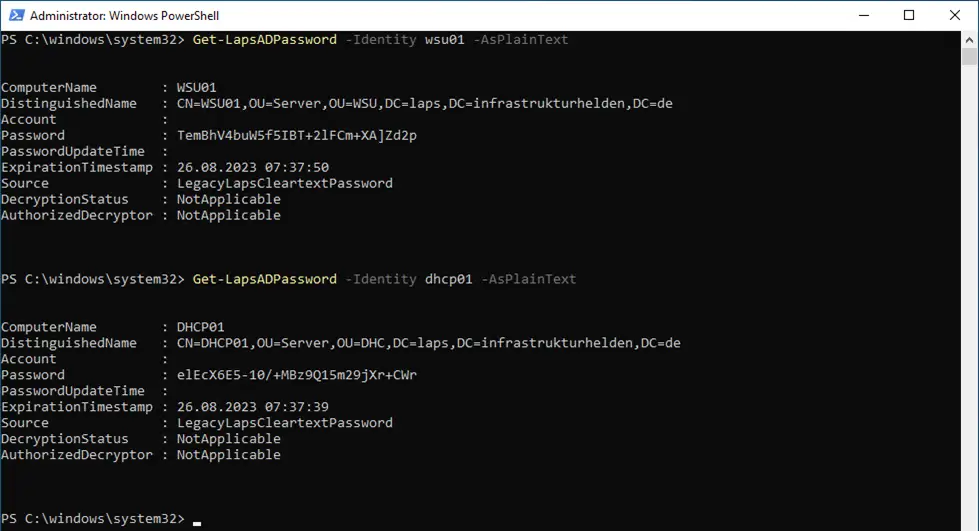
In this era, the topic of IT security is becoming more and more important. A possible attack vector has always been the local admin passwords. In most cases, these were hard-wired into the installation image and had not been changed for years. Not only a risk from former employees. The lateral movement also poses a … Read more